Hackers love to scan WordPress. With millions of outdated installations, picking on WordPress is like bullying the little guy at school. It’s easy and for some – fun to do.
Even if you keep your site updated, you may be surprised about how much information you can extract from a WordPress site.
Gathering information is a key step in any sophisticated attack. Earlier this year, the person that hacked a major security contractor for government’s published a DYI guide to hacking. Many of the steps describe using various tools to gain information about the target.
Server Security Service
If you think your server may have been compromised, rackAID provides security auditing services. While we don’t clean up WordPress code or exploits, we can scan your entire server for malware, rouge processes and more.
We support cPanel, Plesk, Red Hat and CentOS systems. Our comprehensive security audit is just $350 and includes a full Nessus Security scan of your server. If you are struggling to secure your system, contact us for more details.
WordPress Scanning
Gathering information is a key step in any advanced WordPress security attack. Earlier this year, the person that hacked a major security contractor published how they did it. Surprisingly, the attack was not too complex. They used good skills and freely available tools to scan their target.
These tools included simple, freely available scanning tools, Google searches and just looking at the page’s HTML code.
After reading this hacking how-to, I wondered.
What if I turn these tools on a simple WordPress blog?
You may be surprised what your site reveals.
Here’s the results of a simple scan of a WordPress site.
WPScan
WPScan is a WordPress specific security scanner. The scanner can
- Identify Plugins Installed
- Identify Themes Installed
- Enumerate User IDS
- Brute Force Passwords
So what happens if you turn this tool on your typical small business web site.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
|
__ _______ _____
/ / __ / ____|
/ / /| |__) | (___ ___ __ _ _ __
/ / / | ___/ ___ / __|/ _` | '_
/ / | | ____) | (__| (_| | | | |
/ / |_| |_____/ ___|__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version v2.4.1
Sponsored by the RandomStorm Open Source Initiative
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[+] URL: http://www.domain.com/
[+] Started: Tue Sep 16 13:40:36 2014
[+] Interesting entry from robots.txt: /wp-admin/
[+] Interesting entry from robots.txt: /wp-includes/
[+] Interesting header: LINK: <http://www.domain.com/>; rel=shortlink
[+] Interesting header: SERVER: Apache
[+] Interesting header: X-POWERED-BY: PleskLin
[+] XML-RPC Interface available under: http://www.domain.com/xmlrpc.php
[+] WordPress version 4.0 identified from meta generator
[+] Enumerating installed plugins (only vulnerable ones) ...
Time: 00:00:51 <======================================================================================> (824 / 824) 100.00% Time: 00:00:51
[+] We found 4 plugins:
[+] Name: contact-form-7 - v3.9.3
| Location: http://www.domain.com/wp-content/plugins/contact-form-7/
| Readme: http://www.domain.com/wp-content/plugins/contact-form-7/readme.txt
[!] Title: Contact Form 7 & Old WP Versions - Crafted File Extension Upload Remote Code Execution
Reference: http://packetstormsecurity.com/files/125018/
Reference: http://seclists.org/fulldisclosure/2014/Feb/0
Reference: http://osvdb.org/102776
[+] Name: feed
| Location: http://www.domain.com/wp-content/plugins/feed/
[!] Title: Feed - news_dt.php nid Parameter SQL Injection
Reference: http://packetstormsecurity.com/files/122260/
Reference: http://osvdb.org/94804
[+] Name: wordpress-seo - v1.6
| Location: http://www.domain.com/wp-content/plugins/wordpress-seo/
| Readme: http://www.domain.com/wp-content/plugins/wordpress-seo/readme.txt
| Changelog: http://www.domain.com/wp-content/plugins/wordpress-seo/changelog.txt
[!] Title: WordPress SEO 1.14.15 - index.php s Parameter Reflected XSS
Reference: http://packetstormsecurity.com/files/123028/
Reference: http://osvdb.org/97885
[!] Title: WordPress SEO 1.4.6 - Reset Settings Feature Access Restriction Bypass
Reference: http://secunia.com/advisories/52949
Reference: http://osvdb.org/92147
[+] Name: wptouch - v3.3.4
| Location: http://www.domain.com/wp-content/plugins/wptouch/
| Readme: http://www.domain.com/wp-content/plugins/wptouch/readme.txt
[!] Title: WPtouch 3.x - Insecure Nonce Generation
Reference: http://blog.sucuri.net/2014/07/disclosure-insecure-nonce-generation-in-wptouch.html
Reference: http://www.rapid7.com/db/modules/exploit/unix/webapp/wp_wptouch_file_upload
[i] Fixed in: 3.4.3
[+] Enumerating installed themes (only vulnerable ones) ...
Time: 00:00:18 <======================================================================================> (295 / 295) 100.00% Time: 00:00:18
[+] No themes found
[+] Enumerating timthumb files ...
Time: 00:02:32 <====================================================================================> (2532 / 2532) 100.00% Time: 00:02:32
[+] No timthumb files found
[+] Enumerating usernames ...
[+] Identified the following 5 user/s:
+----+----------+------------------+
| Id | Login | Name |
+----+----------+------------------+
| 1 | admin | admin |
| 2 | user1 | user1|
+----+----------+------------------+
[+] Finished: Tue Sep 16 13:44:43 2014
[+] Memory used: 12 MB
[+] Elapsed time: 00:04:06
|
For this site, WPScan found four plugins. Also listed is the current version and past exploit information about the plugin.
Why would you care about past exploit?
If you have a security breach, the best option is to restore from backup. Even if your site is fully updated now, you never now what backdoors attackers may have left due to old exploits.
Previously exploitable plugins may have, in fact, been exploited. If there was some common backdoor used, searching for that file could reveal that the site was previously hacked. For this reason, you should always carefully review any WordPress site after a security breach. Even if you patch the plugin, backdoors can remain. Various scanning tools like maldet can help you find malware but ultimately, the safest solution is to restore from backups.
WPScan also reveals user names. These can be used to start a brute force attack to try to gain direct access to the WP admin area.
Recently, attackers have been using XML-RPC based brute force attacks. These attacks are not blocked by many brute force plugins and require fewer resources than the traditional wp-login.php attacks.
The scan took just four minutes. With a botnet, I could scan 100’s of sites in a few hours. With results in hand, I could either find or write a tool to quickly exploit plugins or brute force the most valuable targets.
[ois skin=”Wordpress Optimization”]
BuiltWith
While attackers often use command line tools to protect their privacy, Builtwith.com is a great information gathering tool.
A key step in any attack is to map out your target. Common questions may include:
- What CMS?
- What OS?
- What web server software?
- What third party tools?
Builtwith.com and other tools make this easy.
Just punch in any web site address and you can find out the web server, hosting provider, CMS and more. By using DNS records, third party email services can be found.

Built With is a free online tool that can quickly map out various technologies and information about a WordPress site.
Sometimes advanced attacks on web sites may start or end elsewhere.
What if an attacker compromises your WordPress blog via a plugin, but through a tool such at Builtwith they know you use Google Apps for email.
They can then start targeting your Google App accounts with data obtained from compromising your blog.
By mapping out the target, attackers can use data from a breach in one service to access another. This is why you should use unique passwords for every site or service you use.
Nikto
Like WPScan, Nikto can find interesting and potentially exploitable items.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
|
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 208.43.95.51
+ Target Hostname: www.domain.com
+ Target Port: 80
+ Start Time: 2014-09-16 13:59:17 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache
+ Retrieved x-powered-by header: PleskLin
+ IP address found in the 'x-mod-pagespeed' header. The IP is "1.8.31.4".
+ The anti-clickjacking X-Frame-Options header is not present.
+ Uncommon header 'link' found, with contents: <http://www.domain.com/>; rel=shortlink
+ Uncommon header 'x-mod-pagespeed' found, with contents: 1.8.31.4-4056
+ Server leaks inodes via ETags, header found with file /robots.txt, inode: 1933349, size: 62, mtime: Wed Jun 11 12:45:15 2014
+ File/dir '/wp-admin/' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ Uncommon header 'x-robots-tag' found, with contents: noindex
+ OSVDB-3092: /updates/: This might be interesting...
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3092: /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /readme.html: This WordPress file reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /wordpress/: A WordPress installation was found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login.php: WordPress login found
+ 7576 requests: 1 error(s) and 20 item(s) reported on remote host
+ End Time: 2014-09-16 14:09:11 (GMT0) (594 seconds)
|
In this report, we find that the server has the WP readme.html file still installed. This quickly tells you what version of WP is in use. Using this data, you could then check to see if there are any known exploits in that version.
This also reveals information about various HTTP headers. For example, mod_pagespeed is active. Does it have any exploits?
By scanning WordPress, attackers can easily learn a lot about how your site is built, the hosting environment and third-party services. Armed with this information, they can begin looking for known exploits.
Exploit Databases
Secunia and similar databases keep track of the various WP security exploits. While you can use them to check the security history of a plugin or find current exploits, attackers can access this information as well.
In some cases, CVE records will reference proof-of-concept exploits. Attackers can use this information to attempt to exploit your WordPress site. With WPScan, it automatically attempts to identify the latest CVE information for any given plugin or theme — providing handy access to this information.
Escalating Access
When an attacker finds an exploit in WordPress, one of their first goals is to escalate their access.
Recently, the popular WP Touch plugin was discovered to have an arbitrary file upload vulnerability. This exploit allows an attacker to upload a file of their choice.
In absence of other security tools, such as Sucuri’s web application firewall, an attacker could upload a PHP Shell Script. Functionally, these PHP shells are nearly the same as an SSH shell. You can change permissions, read files, upload files and more. The tools are very robust.
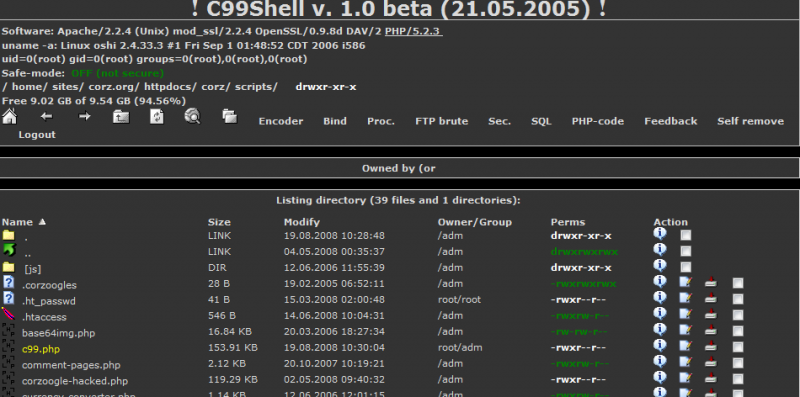
C99Shell is a popular PHP tool designed to escalate access on your server. This is basically a full shell account in PHP.
Another important point about escalated access:
Local exploits become remote exploits when your WordPress site is insecure.
This is why you need to keep any control panels and your OS updated. With a PHP shell kit, an attacker could upload a local OS exploit and execute it. Depending on the type of exploit, they could gain even gain root access.
WP User Security
Many people use the same password for multiple sites. If your WordPress site is breached, then attacker can use your user’s details to compromise their social media accounts, email or even financial sites.
With escalated access, attackers can begin to mine your system for more useful data. What’s useful?
Your WordPress user’s email and passwords.
Attackers can simply export your user’s email and passwords directly from the database. While the passwords are encrypted, simple ones can easily be cracked with password guessing tools.
Many users don’t use unique passwords for different sites. As a result, the attacker has your email address and password. They can then use this information to try to gain access to your email, social media accounts or other popular sites.
As they expand their access, you can become a victim of identify theft, they can use your accounts to spam, host illegal files or more.
Failing to use security in-depth is how a simple WordPress plugin security issue can become a cyber security nightmare.
Advanced Persistent Threats
In the cyber security world, experts like to distinguish between automated attacks and advanced persistent threats (APT). APT are very hard to defend against. With APT, there’s a person at the other end actively trying to find ways into your site or server. Even the smallest clue from their mapping efforts may lead them to a security hole.
Fortunately, for WP users, most people do not face such advanced threats. In fact, in nearly every WP hacking incident we investigate, the attack is done by automated bots that constantly probe for specific exploits.
Blocking these attacks is as simple as keeping your software updated and using good WP security practices.